Microsoft Exchange Server Hack Patch
Exchange Server hack timeline January 3 2021. Theres been a new ransomware attack on an on-premises Microsoft Exchange Server emphasizing once again the need for moving online.
 Ms Exchange Server Hack Worse Than First Thought Information Age Acs
Ms Exchange Server Hack Worse Than First Thought Information Age Acs
Cyber espionage operations against Microsoft Exchange Server begin using the Server-Side Request Forgery SSRF vulnerability CVE-2021-26855.

Microsoft exchange server hack patch. CVE-2021-26855 is a server-side request forgery SSRF vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server. In addition it is now clear when the attack waves started and what could have protected against the hack although four 0-day exploits existed for months. On March 2 Microsoft released patches to tackle four critical vulnerabilities in Microsoft Exchange Server software.
Microsoft detected multiple zero-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks the company said in. The software maker said hackers working on behalf of the Chinese government have been using the previously unknown exploits to hack on-premises Exchange Server software that is fully patched. Microsoft issued patches for four vulnerabilities in its Exchange Server software last Tuesday and said in those initial warnings that the Chinese state-backed hacking group Hafnium was behind the.
CVE-2021-26855 is a server-side request forgery SSRF vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server. Microsoft issued more out-of-band updates for older Microsoft Exchange Server CUs which have already fallen out of support last night. The advanced monitoring capabilities of Exchange are also disabled due to disabling Microsoft Exchange Managed Availability services.
Patching the security gap should be done as quickly as possible but during that it might come to Exchange Server downtime but the email is still the most relevant communication channel for companies of all sizes. This can be used to validate patch and mitigation state of exposed servers. You would think that when Microsoft announced an emergency patch on March 2 to plug four security holes in Exchange Server that any organization using Exchange would have jumped on it.
Detects whether the specified URL is vulnerable to the Exchange Server SSRF Vulnerability CVE-2021-26855. CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. One week ago Microsoft disclosed that Chinese hackers were gaining access to organizations email accounts through vulnerabilities in its Exchange Server email software and issued security.
NSA Uncovers Serious Flaws in Microsoft Exchange Server Urges Public to Patch The four vulnerabilities involve a low attack complexity and can lead to remote code execution enabling a hacker. By downloading and running this tool which includes the latest Microsoft Safety Scanner customers will automatically mitigate CVE-2021-26855 on any Exchange server on which it is. On March 2 Microsoft released emergency security updates to plug four security holes in Exchange Server versions 2013 through 2019 that hackers were actively using to siphon email communications.
Additional hunting and investigation techniques Nmap Script To Scan For CVE-2021-26855. Yet the recent zero-day attack that exploited a Microsoft Exchange security hole highlighted the fact that all is not well in the land of patch management. Microsoft raced out patches for Exchange earlier this month after security researchers discovered that suspected China-backed hackers were exploiting Exchange servers to access emails of targets.
At the time the company said that the bugs were being actively exploited in. This new tool is designed as an interim mitigation for customers who are unfamiliar with the patchupdate process or who have not yet applied the on-premises Exchange security update. In fact according to.
Hackers who went after SolarWinds also breached Microsoft itself The White House is closely tracking an emergency patch Microsoft Corp has released US national security adviser Jake Sullivan said. The emergency security patch Microsoft rolled out a few days ago to fix four zero-day flaws in Exchange Server didnt deter the hacking group thats been exploiting them. The Federal Office for Information Security BSI calls on operators of the affected Exchange systems to immediately apply the patches provided by Microsoft.
 Microsoft Exchange Server Hack What You Need To Know And Do Now Creo Inc Creo Inc
Microsoft Exchange Server Hack What You Need To Know And Do Now Creo Inc Creo Inc
 Hackers Scanning For Vulnerable Microsoft Exchange Servers Patch Now
Hackers Scanning For Vulnerable Microsoft Exchange Servers Patch Now
 Infosec Alert Microsoft Exchange Server Hack Miller Kaplan
Infosec Alert Microsoft Exchange Server Hack Miller Kaplan
 Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
 Microsoft Exchange Server S Hacked
Microsoft Exchange Server S Hacked
 The Microsoft Exchange Hacks How They Started And Where We Are
The Microsoft Exchange Hacks How They Started And Where We Are
 How The Microsoft Exchange Hack Could Impact Your Organization Techrepublic
How The Microsoft Exchange Hack Could Impact Your Organization Techrepublic
 Microsoft Shares One Click Mitigation Tool For Exchange Server Flaws
Microsoft Shares One Click Mitigation Tool For Exchange Server Flaws
 Microsoft Chinese Hackers Are Exploiting Exchange Server Flaws To Steal Emails
Microsoft Chinese Hackers Are Exploiting Exchange Server Flaws To Steal Emails
 This New Microsoft Tool Checks Exchange Servers For Proxylogon Hacks
This New Microsoft Tool Checks Exchange Servers For Proxylogon Hacks
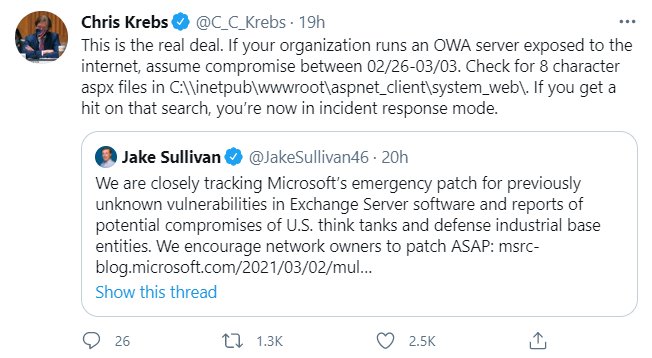 At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security
At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security
 Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
 Exchange Server Hack Goes From Bad To Worse Securedata
Exchange Server Hack Goes From Bad To Worse Securedata
 Accelerate Secops Investigation And Response To The Microsoft Exchange Server Attack With Cortex Xsoar Palo Alto Networks Blog
Accelerate Secops Investigation And Response To The Microsoft Exchange Server Attack With Cortex Xsoar Palo Alto Networks Blog
 Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
 Microsoft Exchange Servers Hacked What You Should Know And Do
Microsoft Exchange Servers Hacked What You Should Know And Do
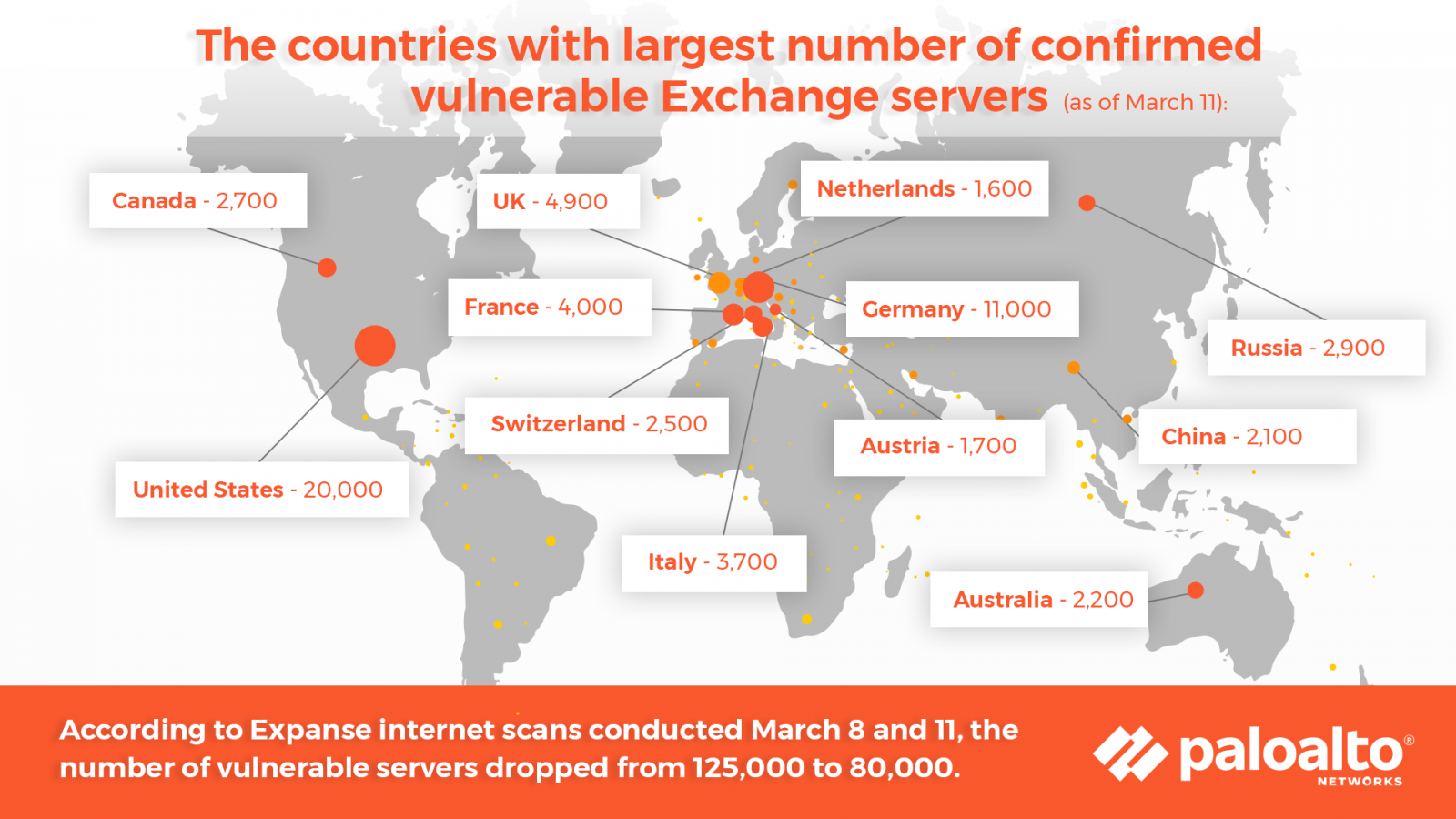 The Microsoft Exchange Hacks How They Started And Where We Are
The Microsoft Exchange Hacks How They Started And Where We Are
 Attack On Exchange Servers Gives Impetus To Move Email To The Cloud
Attack On Exchange Servers Gives Impetus To Move Email To The Cloud
 Microsoft Exchange Server Hafnium Zero Day Hack Swat Systems
Microsoft Exchange Server Hafnium Zero Day Hack Swat Systems
Post a Comment for "Microsoft Exchange Server Hack Patch"