Microsoft Exchange Hack Statement
Administrators can use this tool for servers not protected by Microsoft. They were using a vulnerable Microsoft program Credit.
March 2021 Microsoft Exchange Server Hack How To Remediate Get Help Opkalla
An espionage group has hacked some 30000 US organizations over the past few days KrebsOnSecurity reported.

Microsoft exchange hack statement. After months of Microsoft Exchange drama thanks to the Microsoft Exchange Server hacks at the hands of multiple groups. SOPA ImagesLightRocket via Gett. Microsoft said the Exchange flaws are being targeted by a previously unidentified Chinese hacking crew it dubbed Hafnium and said the group had been conducting targeted attacks on email systems.
Exchange Server is primarily used by business customers and we have no evidence that Hafniums activities targeted individual consumers or that these exploits impact other Microsoft products. Even though weve worked quickly to deploy an update for the Hafnium exploits we know that many nation-state actors and criminal groups will move quickly to take. Microsoft issued more out-of-band updates for older Microsoft Exchange Server CUs which have already fallen out of support last night.
Microsoft Defender has included security intelligence updates to the latest version of the Microsoft Safety Scanner MSERTEXE to detect and remediate the latest threats known to abuse the Exchange Server vulnerabilities disclosed on March 2 2021. Microsoft released several security updates to its Exchange email product to combat the. At the time of this release Microsoft released a statement saying the bugs were being actively exploited in limited targeted attacks.
CISA and Microsoft encourages organizations to upgrade their on-premises Exchange environments to the latest supported version. In the attacks observed the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts and allowed installation of additional malware to facilitate. Storting hacked through Exchange server Soon after suffering a cyberattack in December the Storting today announced a new cyberattack linked to the recent Microsoft Exchange vulnerabilities.
A massive espionage spree by a state-sponsored Chinese hacking group has hit at least 30000 victims in the United States alone. Microsoft Exchange seems to be linked to the root of the cyberattack. Coalition evaluated Colonial Pipeline and found numerous potential risks that could have led to the breach.
The breach started with a group of state-sponsored hackers attributed to China known as. The most likely culprit is vulnerable Microsoft Exchange. The Exchange Server vulnerabilities leveraged by the group known as.
They were running on-premises versions of Microsoft Exchange Server software used to provide enterprise-level email service. Microsoft Support Emergency Response Tool MSERT to scan Microsoft Exchange Server. A week after Microsoft announced that its widely used email server program had been hacked experts are not encouraged by what they have found.
In summary Microsoft says that attackers secure access to an Exchange Server either through these bugs or stolen credentials and they can then create a web shell to hijack the system and execute. In addition it is now clear when the attack waves started and what could have protected against the hack although four 0-day exploits existed for months. March 17 2021.
HOUSTON Authorities have executed a court-authorized operation to copy and remove malicious web shells from hundreds of vulnerable computers in the United States. In short its gotten really messy said Katie. A forensic report noted that the most likely culprit within the companys IT infrastructure was the vulnerable Microsoft Exchange services as noted by New York Times reporter Nicole Perlroth.
On March 2 2021 Microsoft released patches to tackle four server vulnerabilities in Microsoft Exchange software. Private company Colonial issued a statement following the news insisting that the pipeline was still using a vulnerable version of Microsoft Exchange prior to the shortage. Microsoft has released alternative mitigation techniques for Exchange Server customers who are not able to immediately apply updates that address vulnerabilities disclosed on March 2 2021.
Through January and February 2021 certain hacking groups exploited zero-day vulnerabilities in Microsoft Exchange. Over the past two weeks Microsoft clients using its Exchange servers which includes tens of thousands of government agencies and private corporations around the world have fallen victim to a series of hacks that have compromised their data. Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks.
 Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
 Petya Ransomware Authors Demand 250 000 In First Public Statement Since The Attack Microsoft Exchange Server Face Id Computer Security
Petya Ransomware Authors Demand 250 000 In First Public Statement Since The Attack Microsoft Exchange Server Face Id Computer Security
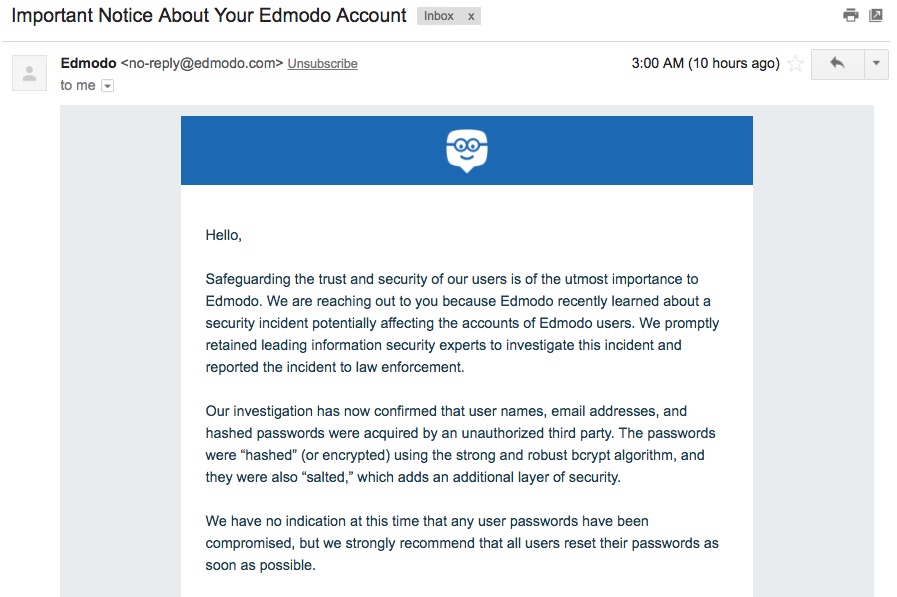 77 Million Edmodo Users Are Hacked As Widespread Cyberattacks Hit The Ed Tech World The 74
77 Million Edmodo Users Are Hacked As Widespread Cyberattacks Hit The Ed Tech World The 74
 Microsoft Exchange Cyber Attack What Do We Know So Far
Microsoft Exchange Cyber Attack What Do We Know So Far
 32 Million Hack Crypto Exchange Bitpoint Hit Cryptobuzz Tech Hacks About Me Blog How To Find Out
32 Million Hack Crypto Exchange Bitpoint Hit Cryptobuzz Tech Hacks About Me Blog How To Find Out
 Accelerate Secops Investigation And Response To The Microsoft Exchange Server Attack With Cortex Xsoar Palo Alto Networks Blog
Accelerate Secops Investigation And Response To The Microsoft Exchange Server Attack With Cortex Xsoar Palo Alto Networks Blog
 8 Outlook Hints Everyone Should Know Outlook Calendar Outlook Hacks Microsoft Outlook
8 Outlook Hints Everyone Should Know Outlook Calendar Outlook Hacks Microsoft Outlook
 What A Phishing Email Looks Like And How To Detect One Infographic Cyber Security Awareness Computer Security Cyber Security
What A Phishing Email Looks Like And How To Detect One Infographic Cyber Security Awareness Computer Security Cyber Security
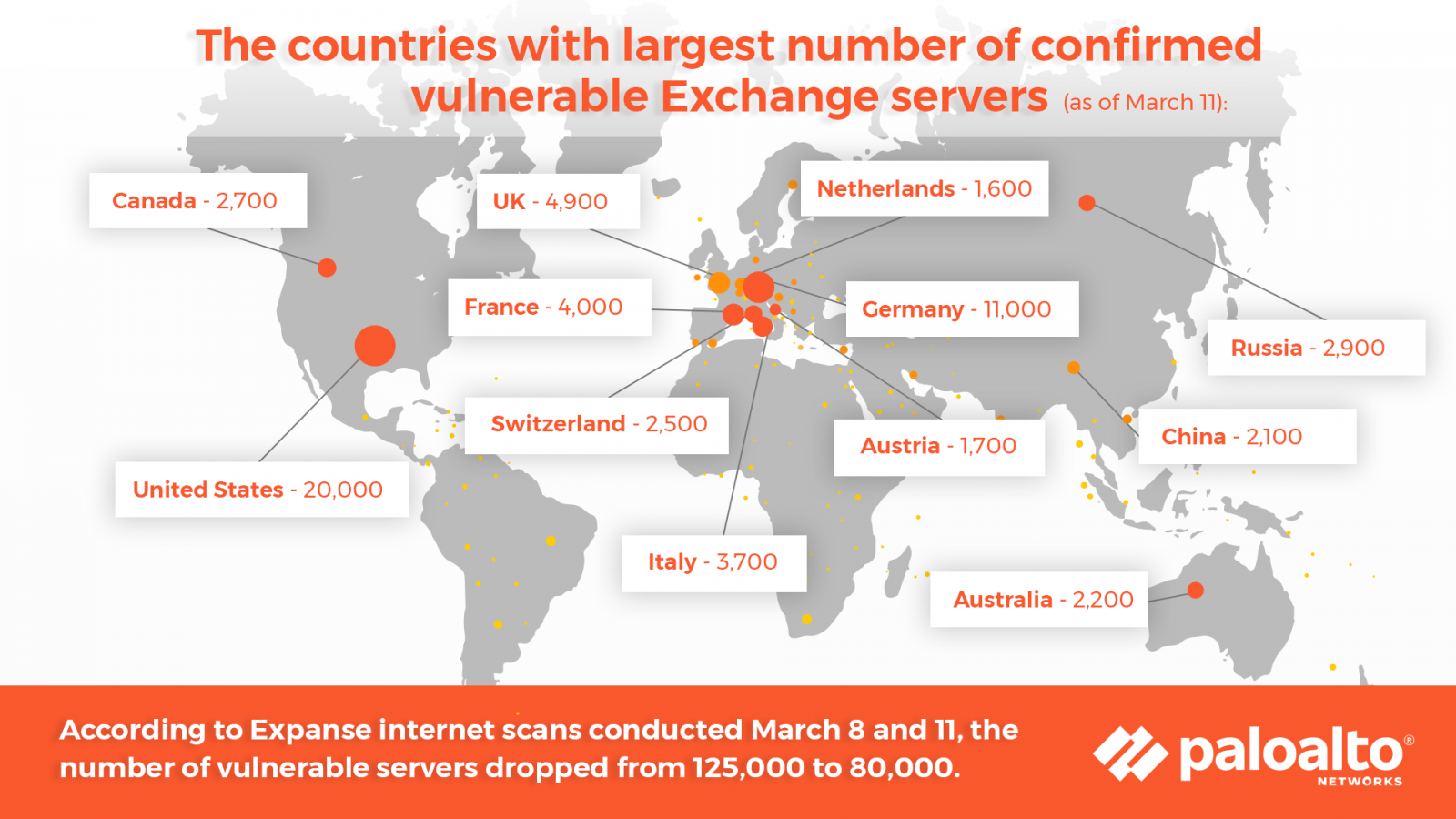 The Microsoft Exchange Hacks How They Started And Where We Are
The Microsoft Exchange Hacks How They Started And Where We Are
 Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
Exchange Hack News Test Tools From Microsoft And Others Born S Tech And Windows World
 What To Know About The Microsoft Exchange Hack
What To Know About The Microsoft Exchange Hack
 This New Microsoft Tool Checks Exchange Servers For Proxylogon Hacks
This New Microsoft Tool Checks Exchange Servers For Proxylogon Hacks
 Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
Microsoft Exchange Server Hacked What Are The Consequences Techzine Europe
 The Microsoft Exchange Hacks How They Started And Where We Are
The Microsoft Exchange Hacks How They Started And Where We Are
 Microsoft Exchange Hack Larger Than Originally Believed Prompts Emergency Task Force Siliconangle
Microsoft Exchange Hack Larger Than Originally Believed Prompts Emergency Task Force Siliconangle
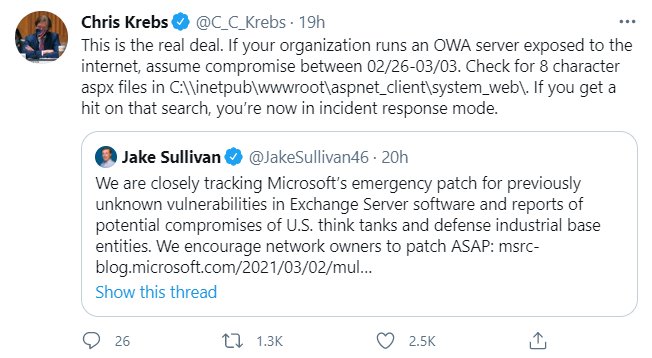 At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security
At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security
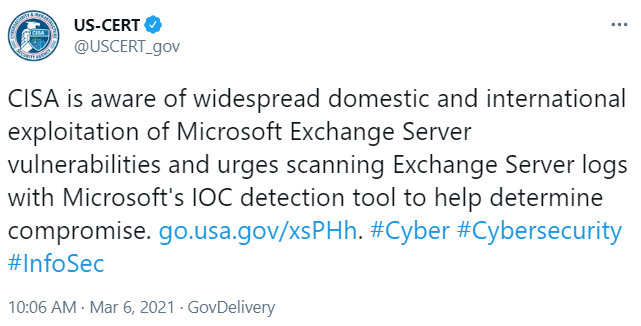 At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security
At Least 30 000 U S Organizations Newly Hacked Via Holes In Microsoft S Email Software Krebs On Security


Post a Comment for "Microsoft Exchange Hack Statement"