Zero-trust Security Principles For Microsoft 365
Guiding principles of Zero Trust. Secure identity with Zero Trust.
 How Microsoft Does Zero Trust Youtube
How Microsoft Does Zero Trust Youtube
For simplicity this document will focus on ideal deployments and configuration.
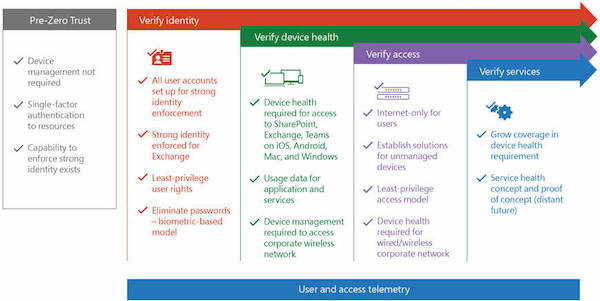
Zero-trust security principles for microsoft 365. Microsoft Advanced Compliance Solutions in Zero Trust Architecture Zero Trust architecture starts with Identity and Access Management but it doesnt end there. Build Zero Trust into your organization min. The different areas are.
Microsoft 365 Zero Trust Microsoft 365 as a core service adheres to Zero Trust Networking. Microsoft have made a strong commitment to Zero-Trust principles throughout their solutions. Microsoft Azure Government has developed a 12-step process for securing identity and access management in federal information systems which is aligned with the identity management principles within the NIST OMB and CISA Zero Trust frameworks.
Intermediate understanding of Microsoft 365 and Azure Active Directory. Introduction to Zero Trust min. Its is divided by area and explains why and how you should implement certain security features and products to enable Zero Trust.
At Microsoft we define Zero Trust around universal principles. The Microsoft Zero Trust Deployment Center is the one-stop-shop for all Microsoft Zero Trust content. To understand the guiding principles of Zero Trust.
Microsoft Zero Trust Security Instead of believing everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an uncontrolled network. Regardless of where the request originates or what resource it accesses Zero Trust teaches us to never trust always verify. A foundational building block of how organizations can implement Zero Trust within Microsoft 365 is Azure Active Directory Conditional Access.
Explore the Zero Trust approach to security in Microsoft 365. Below are the 4 principles at a high level. Use least privileged access.
Many of the core features needed to execute an organization-wide Zero Trust policy are available across Microsoft 365 giving admins the tools they need to continuously and autonomously verify user identities and segment access to sensitive data. In our previous guidance for managing Microsoft 365 traffic endpoints were organized into two categories Required and OptionalEndpoints within each category required different optimizations depending on the criticality of the service and many customers faced challenges in justifying the application of the same network optimizations to the full list of Office 365. This module examines the concepts and principles of the Zero Trust security model as well as how Microsoft 365 supports it and how your organization can implement it.
Microsofts phased implementation of Zero Trust centers on strong user identity device health verification validation of application health and secure least-privilege access to corporate resources and services. To dive into the details please watch the first video in our Microsoft 365 Network Connectivity Video Series embedded in this blog. Implementing Zero Trust at Microsoft Microsoft deployed Zero Trust to secure corporate and customer data.
Always authenticate and authorize based on all available data points. Guiding principles of Zero Trust. The core principle of Zero Trust is maintaining strict access control.
Limit user access with Just-In-Time and Just-Enough-Access JITJEA risk-based adaptive policies and data protection. To explain how the Zero Trust mindset improves your security posture. Microsoft Advocates Zero Trust Security for Hybrid Networks Microsoft this week highlighted the general trend toward implementing hybrid networks which is the combined use of cloud services.
This concept is critical to prevent attackers from pivoting laterally and elevating access within an environment. Please watch out for additional videos that dive deep into the details on how those principles can be applied to network design network configuration remote user. Microsoft is providing a series of deployment guides for customers who have engaged in a Zero Trust security strategyIn this guide we cover how to deploy and configure Azure Active Directory Azure AD capabilities to support your Zero Trust security strategy.
By implementing Zero Trust Microsoft takes a layered approach to secure corporate and customer data. Microsoft Advanced Compliance solutions complement Azure Active Directory and Conditional Access with important protections around the data applications and network pillars. The implementation centered on strong user identity device health verification validation of application health and secure least-privilege.
 How To Get Started With Zero Trust In Microsoft 365 Daniel Chronlund Cloud Tech Blog
How To Get Started With Zero Trust In Microsoft 365 Daniel Chronlund Cloud Tech Blog
 Microsoft Zero Trust Security Youtube
Microsoft Zero Trust Security Youtube
 Preparing For The Ms 900 Microsoft 365 Fundamentals Exam April 2021 Update Intunedin Net
Preparing For The Ms 900 Microsoft 365 Fundamentals Exam April 2021 Update Intunedin Net
 Cloud Architekt Net Implementing Zero Trust With Microsoft 365 Study Collection
Cloud Architekt Net Implementing Zero Trust With Microsoft 365 Study Collection
 Study Guide Ms 900 Microsoft 365 Fundamentals
Study Guide Ms 900 Microsoft 365 Fundamentals
 What Is Zero Trust Security Coreview
What Is Zero Trust Security Coreview
 Assessing Microsoft 365 Security Solutions Using The Nist Cybersecurity Framework Microsoft Security
Assessing Microsoft 365 Security Solutions Using The Nist Cybersecurity Framework Microsoft Security
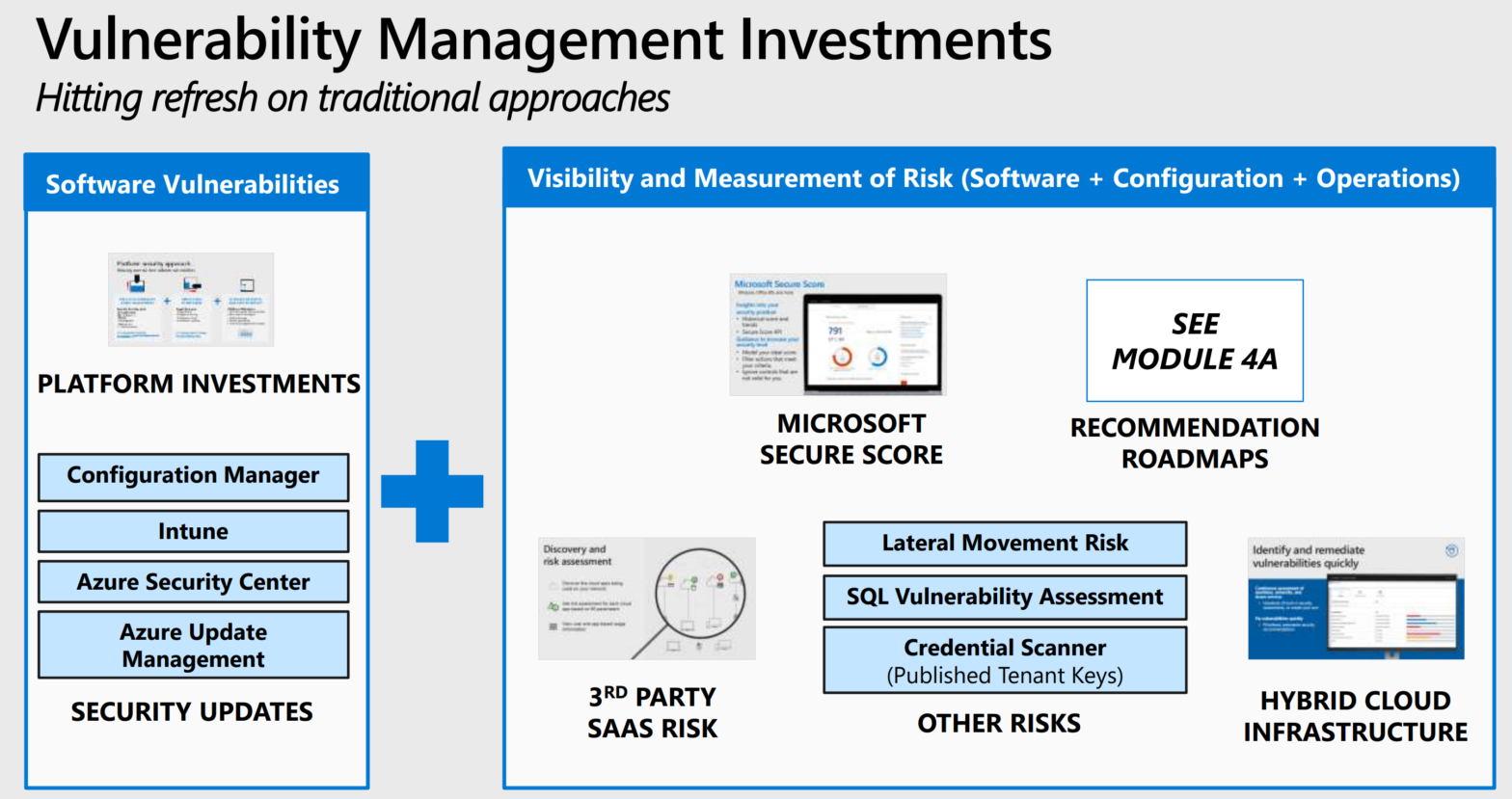 Best Zero Trust Sources Microsoft 365 Azure Jasper Bernaers
Best Zero Trust Sources Microsoft 365 Azure Jasper Bernaers

 Protecting Microsoft 365 From On Premises Attacks Techevangs
Protecting Microsoft 365 From On Premises Attacks Techevangs
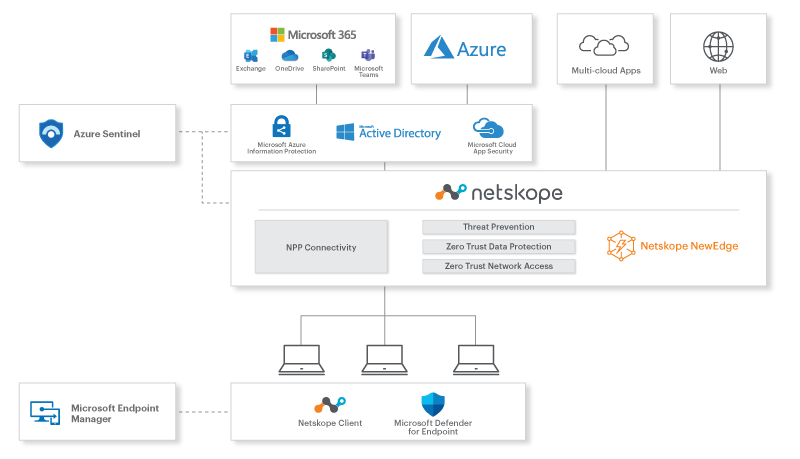 Netskope Partner Microsoft Netskope
Netskope Partner Microsoft Netskope
 What Is The Microsoft Zero Trust Security Model Thirdspace Blog
What Is The Microsoft Zero Trust Security Model Thirdspace Blog
 Implementing A Zero Trust Security Model At Microsoft Cloud Based Services Device Management Virtual Private Network
Implementing A Zero Trust Security Model At Microsoft Cloud Based Services Device Management Virtual Private Network
 The Top 10 Zero Trust Security Solutions Expert Insights
The Top 10 Zero Trust Security Solutions Expert Insights
 When And Why Should You Start With Microsoft 365 Business Premium
When And Why Should You Start With Microsoft 365 Business Premium
 How Microsoft Does Zero Trust Youtube
How Microsoft Does Zero Trust Youtube
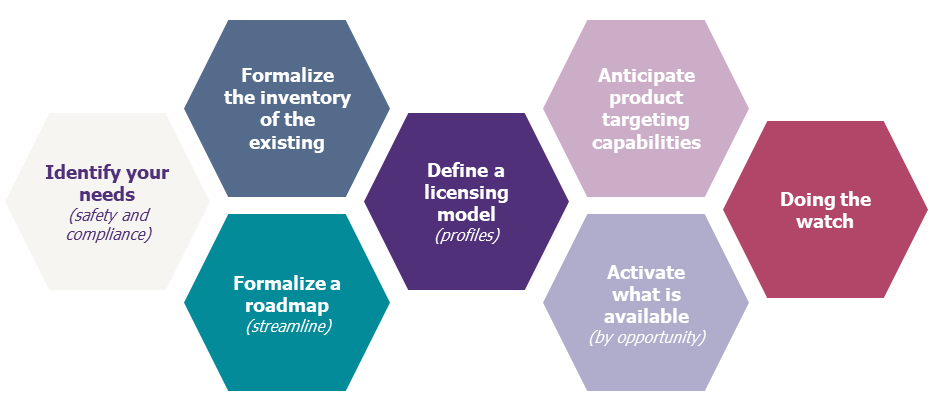 A Short Guide To The Jungle Of Microsoft 365 Security And Compliance Licensing Part 2 Riskinsight
A Short Guide To The Jungle Of Microsoft 365 Security And Compliance Licensing Part 2 Riskinsight
 Common Identity And Device Access Policies Microsoft 365 For Enterprise Office 365 Microsoft Docs
Common Identity And Device Access Policies Microsoft 365 For Enterprise Office 365 Microsoft Docs
 Assessing Microsoft 365 Security Solutions Using The Nist Cybersecurity Framework Microsoft Security
Assessing Microsoft 365 Security Solutions Using The Nist Cybersecurity Framework Microsoft Security
Post a Comment for "Zero-trust Security Principles For Microsoft 365"